Infiniti Azure AD SAML Extension
Deployment Feature AvailabilityAvailable in on-premise and private instance cloud deployments only.
Interface Feature AvailabilityAvailable in web interfaces Produce, Manage and Design only.
The Infiniti Azure AD SAML Extension provides a seamless authentication and authorization experience for Azure AD users.
This extension leverages SAML 2.0 to perform user authentication, which involves redirecting the user’s browser to the Azure AD login page and, on successful authentication, redirecting back to Infiniti where the extension will parse the SAML claims, identifying the user.
Infiniti provides a built-in SAML implementation which can work with Azure AD, however this extension provides the following key differences that are important for some implementations:
- Configuration is performed at the site level, allowing mixed authentication modes by creating additional sites. For example, having one Azure AD authenticated Produce instance and another that uses forms authentication.
- Being specific for Azure AD, it is capable of calling the Microsoft Graph API to retrieve user group information allowing group-based authorization.
This guide provides configuration information for installing the extension and getting started with it, covering Infiniti configuration and where to find key information from Azure AD in the Azure portal.
It is important to know that Azure AD SAML is for User Authentication is only, it does not enable Active Directory synchronization of Users and Groups.
Note that this guide is not a comprehensive guide for using Azure AD and all its features, so please refer to Microsoft’s Azure AD documentation for more details on that platform.
Version History
Version 1.3.0.0 (released 12 Oct 2018)
- Modified to be compatible with Infiniti 10.1+ User Profile Settings engine
Version 1.0.1.0 (released 13 Feb 2018)
- Initial release
Azure AD Configuration
This article covers app registration for adding Infiniti Produce or Manage to an existing Azure AD instance.
Note that if you intend to use Azure AD SAML Authentication for both Manage AND Produce, you will need to create two separate App Registrations. The procedure is similar for both.
- In the Azure portal go to the Azure Active Directory and navigate to App Registrations > New Application Registration.
- Provide a unique name for the Infiniti Manage app, e.g. ‘Infiniti with AzAD Auth - Manage’.
- Select whether the App Registration will be used with just the current Azure AD tenancy or others.
- In the Redirect URI, select 'Web' as the Application Type. Enter the URL for the Infiniti Manage site as the URL, e.g. ‘https://server/Manage’.
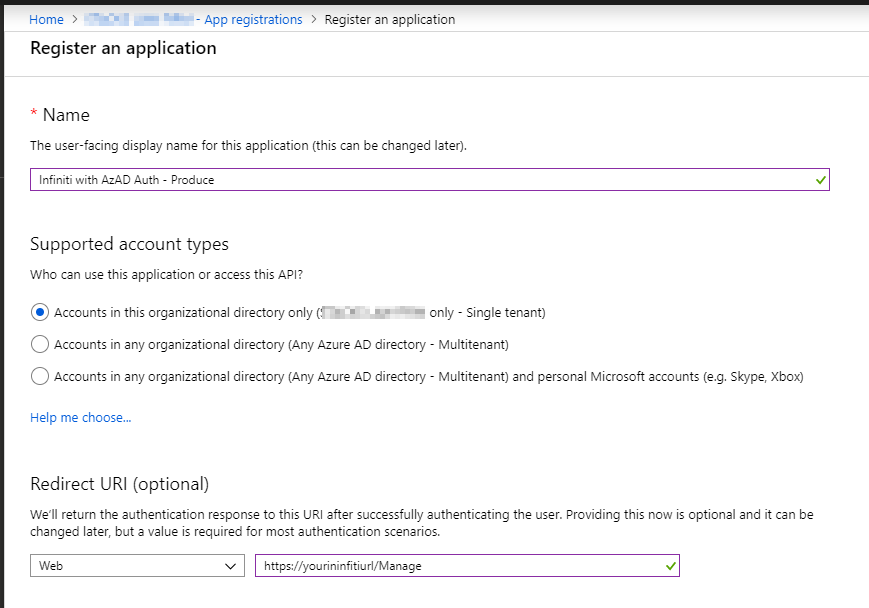
- Click Register to create the app registration.
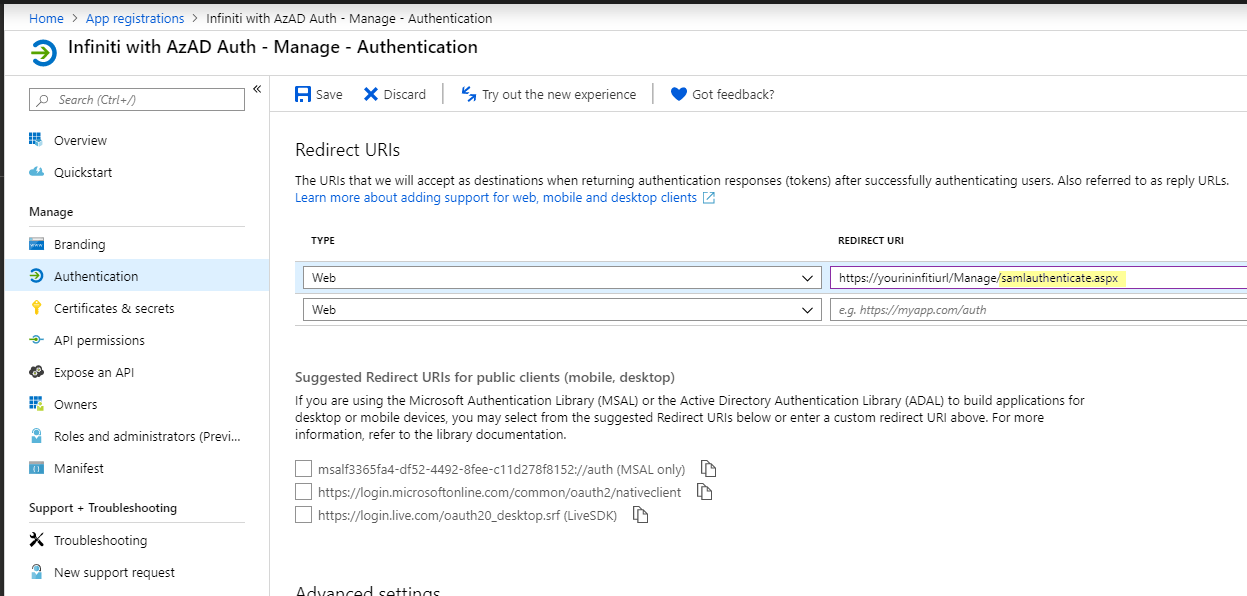
Once the App Registration is complete, you will be redirected to it. - From the new registered app, click Authentication. Update the Redirect URL to point to the ‘samlauthenticate.aspx’ page in your site, e.g. ‘https://server/Manage/samlauthenticate.aspx’.
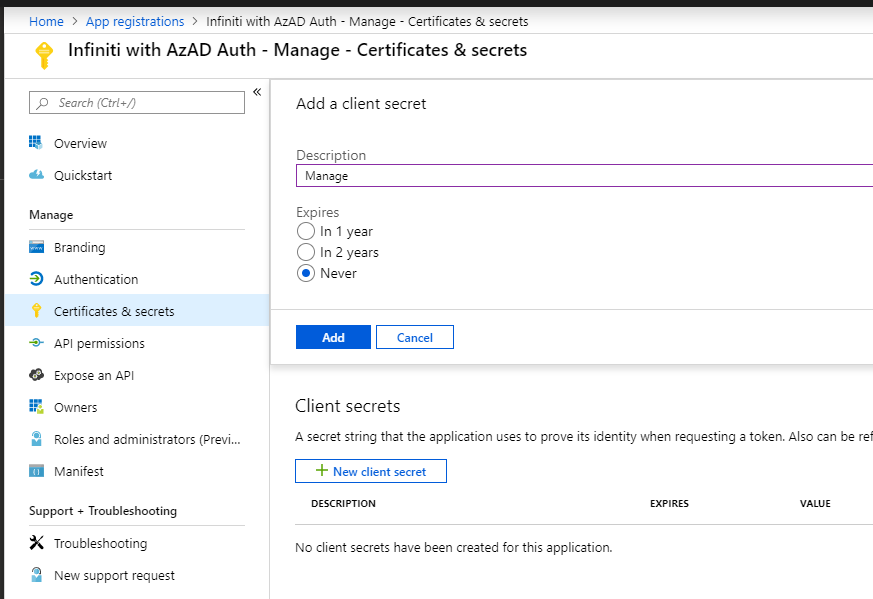
- Navigate to Certificates & secrets to create a new Client secret for the system to use to access the Graph API.
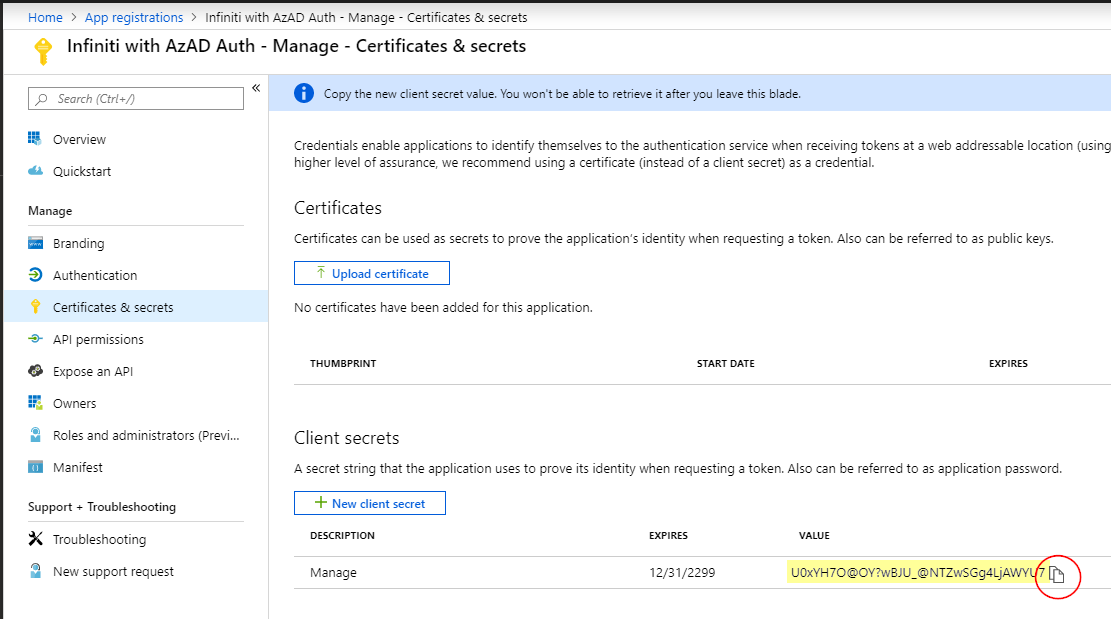
- Click New client secret, enter a description e.g. ‘Manage’ and select an appropriate duration (note that after expiry, a new password will be needed to continue operation), then click Add. A new hashed secret will be displayed for you to copy and save for later use in the Infiniti Manage appsettings.json file. This will be your "AppKey" in the JSON file... record it in the note taking system of your choice.
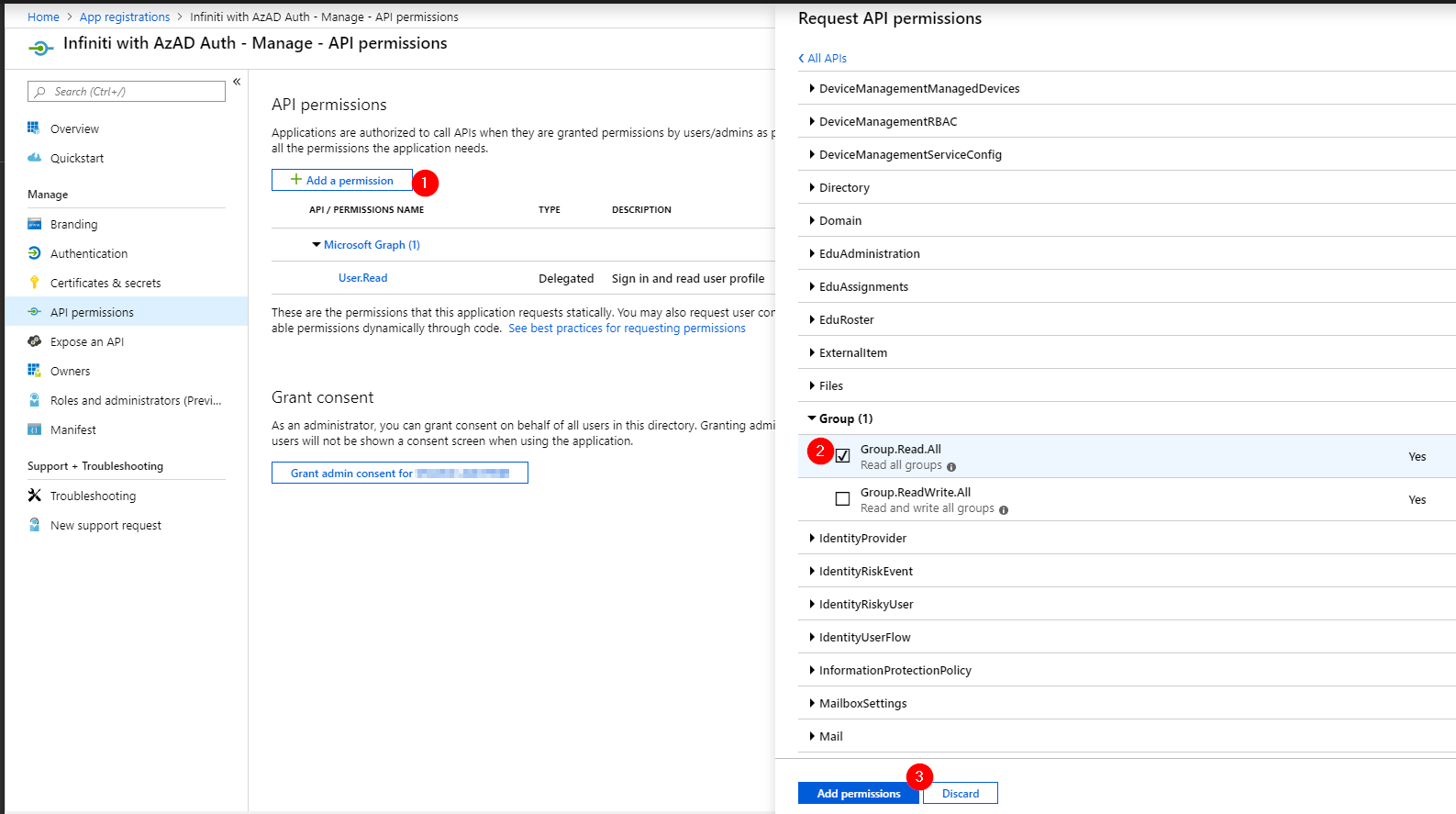
- Navigate to API permissions to configure access to Microsoft Graph, which is used to retrieve Azure AD user group information. Click Add a permission [1] and then select Microsoft Graph from the 'Commonly used Microsoft APIs' list. Then select Application permissions; scroll down, locate and click Group, then place a tick in Group.Read.All [2]. Lastly, click Add permission [3].
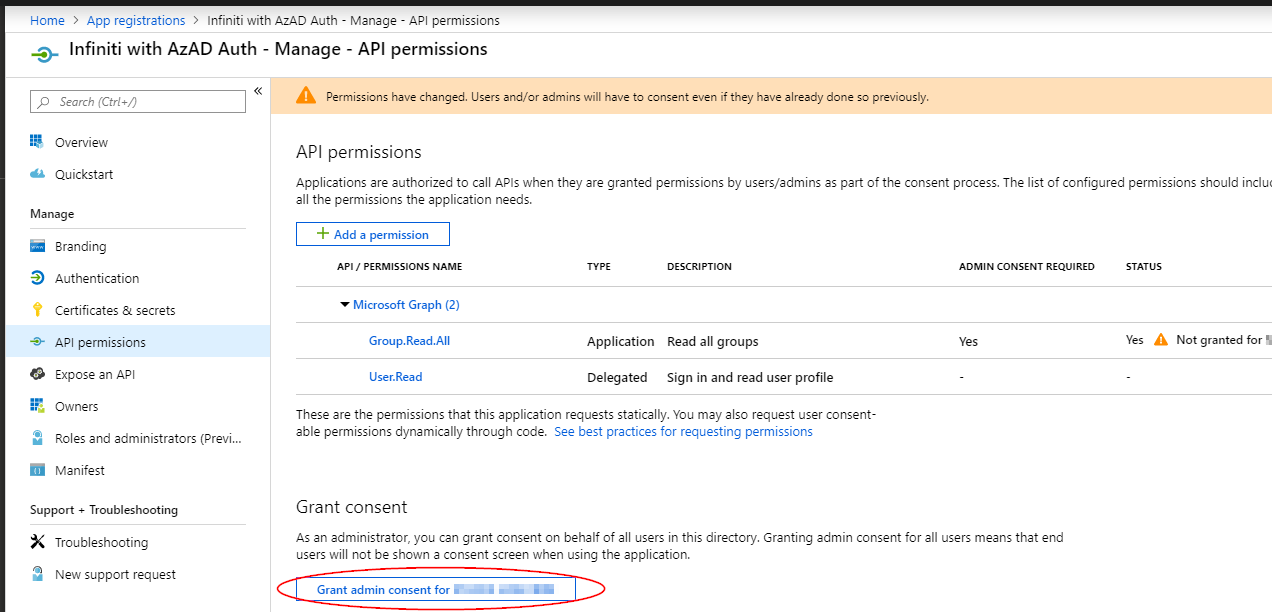
- While still on the API permissions page, click Grant admin consent for (...) to grant permissions to all users. Click YES to confirm. The STATUS column should now have green ticks for both API permissions listed.
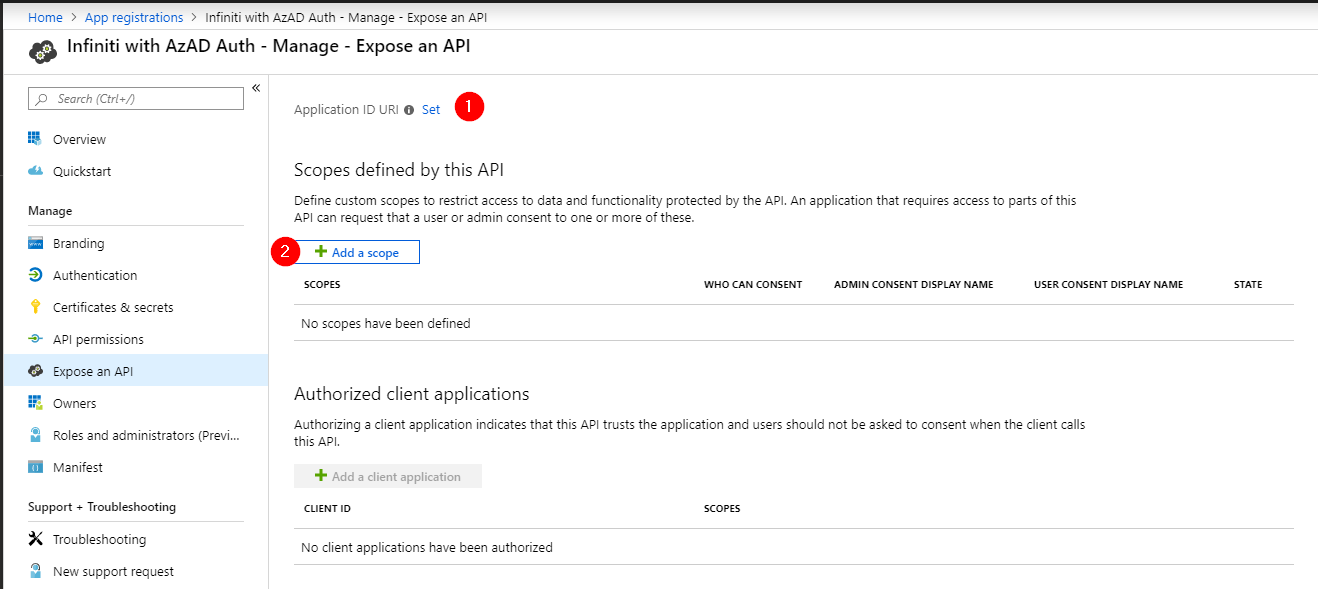
- Navigate to the Expose an API section. Click Set to enable and set the Application ID URI [1]. Keep the automatically inserted ID and click Save. Once generated, record this in your note taking system as it will be the "Manage Entity ID" in the Infiniti SAML Settings configuration and also the "RequestIssuerAppId" value in the Manage appsettings.json file later on.
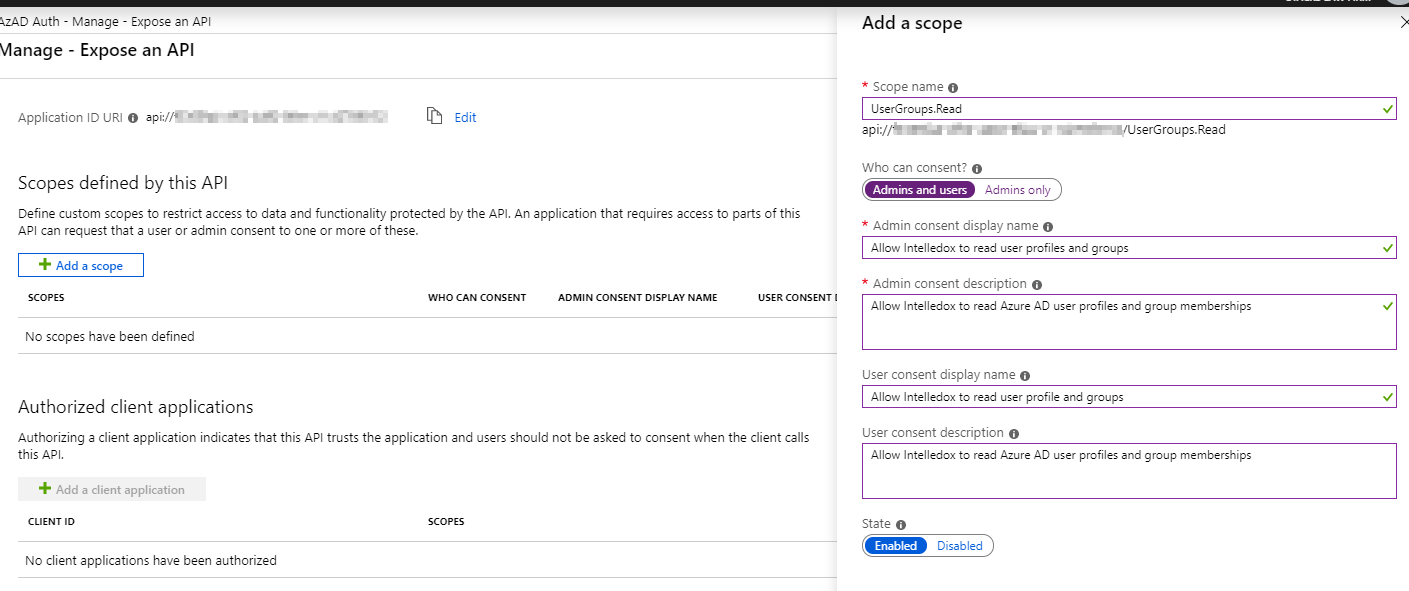
- Click Add a scope [2] , define a scope name (eg. UserGroups.Read), change the consent to Admins and users, define a display name and description for both admins and users (see screenshot below for example), then click Add scope.
- Navigate to the Manifest and modify the "groupMembershipClaims" value from null to "SecurityGroup" (with quotations), then click Save.
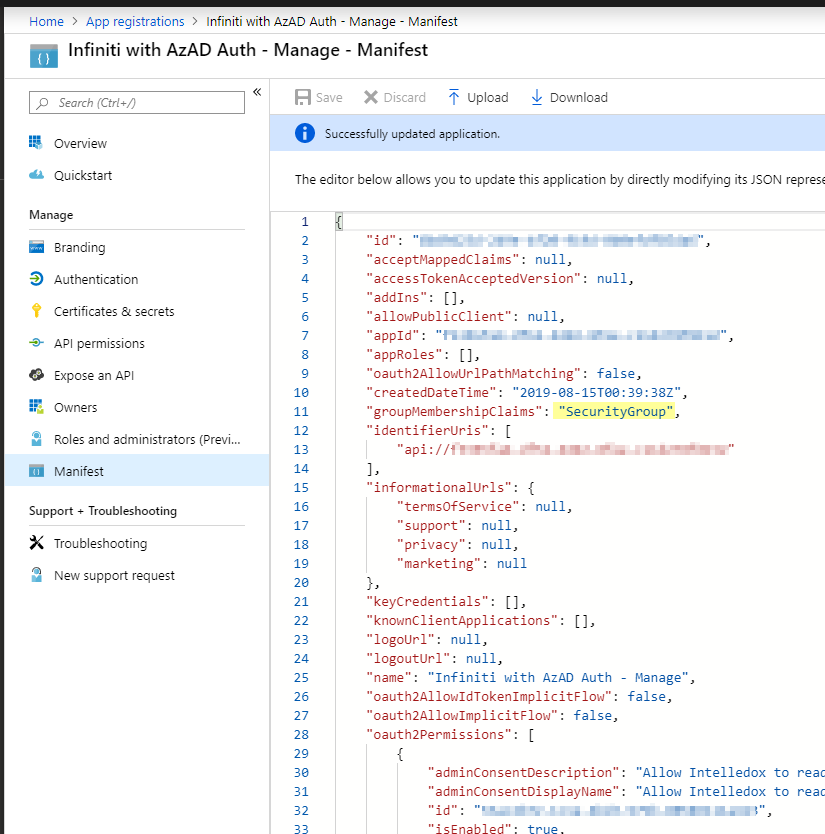
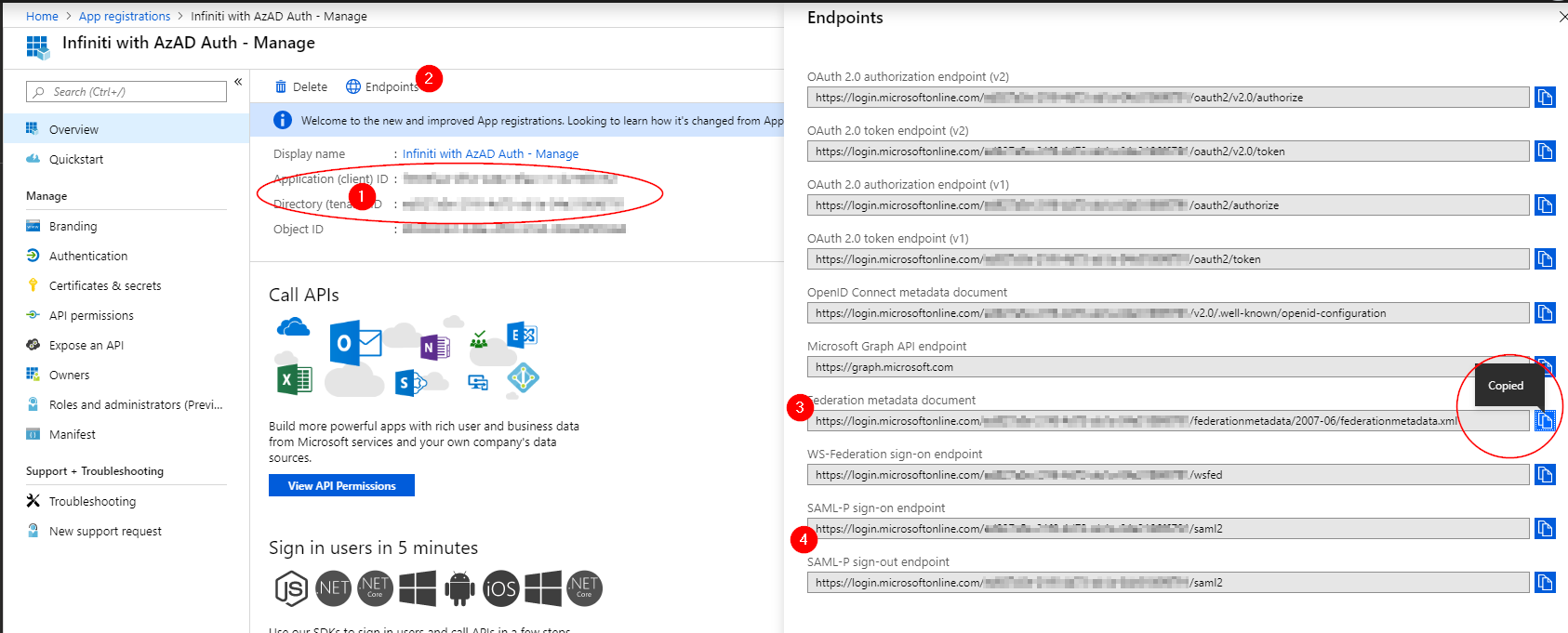
Whilst still in the Azure App Registration, click on the Overview section, and record in your notes both the Application (client) ID and the Directory (tenant) ID [1}. These will be your "ApplicationID" and "DirectoryID" in the the Manage app's appsetting.json file.
- Click Endpoints, then copy the URL for the "Federation metadata document" [3]. Record it in your note system for later use. Also record the "SAML-P sign-on endpoint" [4] value (it's the same as the sign-out value). These will be the "Metadata Url" value and the "Identity Provider Login" values in the Infiniti SAML Settings config later, as well as the "FederationMetadataURL" value and the "IdentityProviderLoginUrl" values in the Manage appsettings.json file.
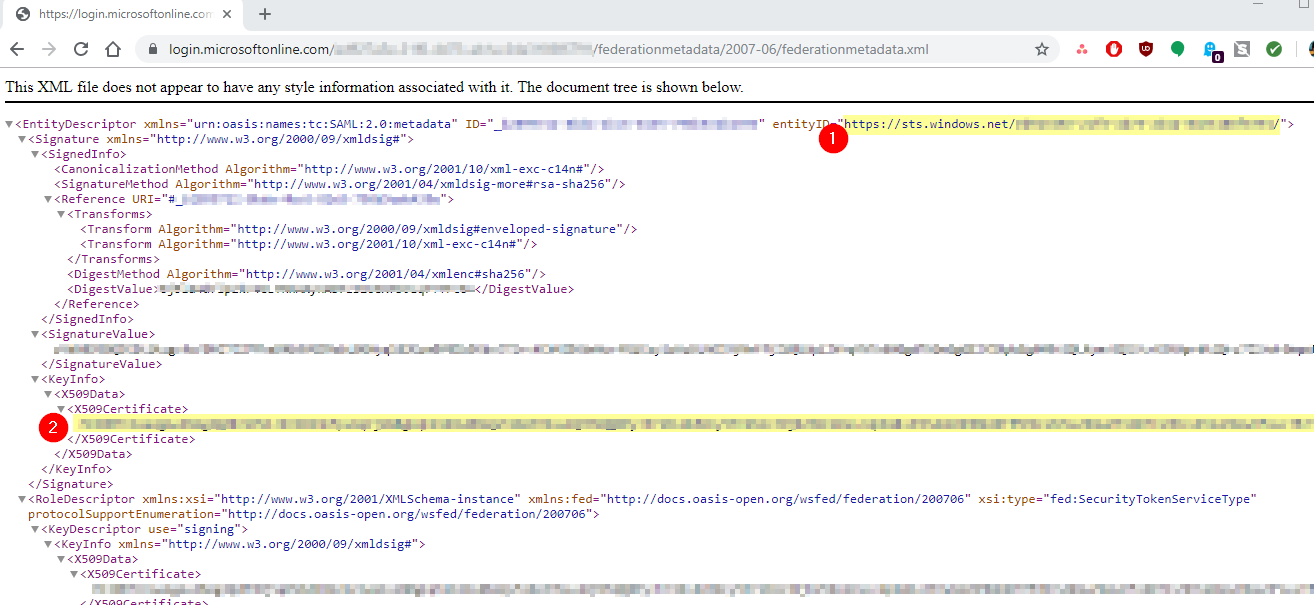
- Open a new browser tab and paste this same Federation Metadata URL [3 in above screenshot] into the address bar and go to the document.
- In the first line, locate the URL for "entityID" and copy the full URL [1 below] into your notes. This will be used in the "Identity Provider Issuer" field later on during the Infiniti SAML Settings configuration.
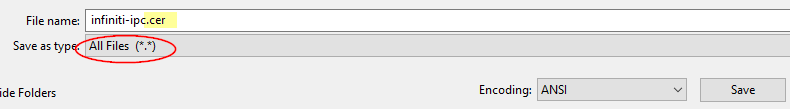
- While here, also copy the string found in Signature > KeyInfo > X509Data > X509Certificate (see screenshot below for exact location) [2]. It's quite long, so ensure that you copy the entire string exactly as is. Open a new notepad document and paste the string into it as is. Save the notepad file somewhere on your computer as "infiniti-ipc.cer" (note the file extension is .cer). This certificate file will need to be uploaded into the Infititi SAML settings configuration later on as the "Identity Provider Certificate".
Infiniti SAML 2.0 Configuration
Now that you have a number of notes and a certificate ready for use, login to Infiniti Manage with a Global Admin account.
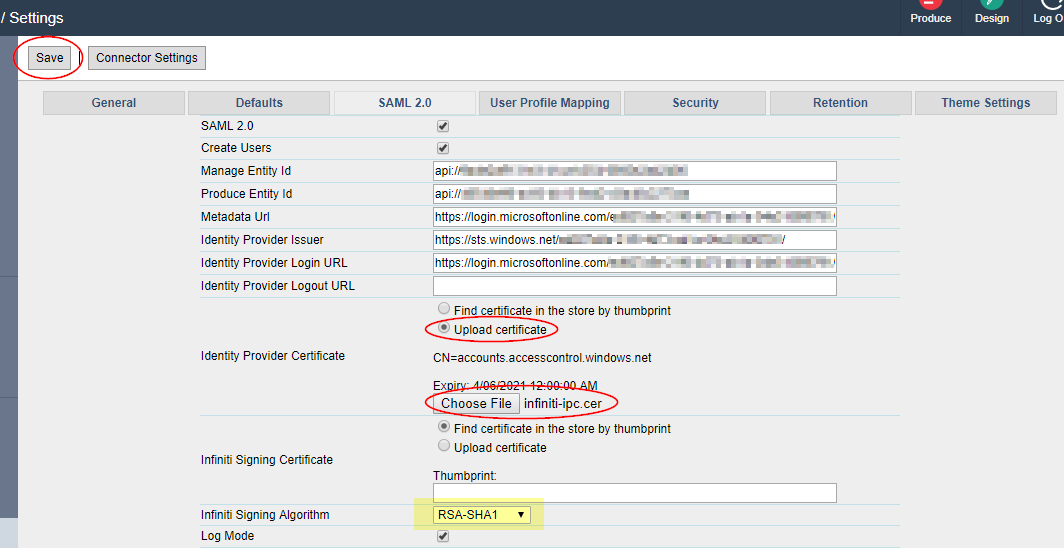
Navigate to Settings > SAML 2.0.
- Tick "SAML 2.0" and "Create users"
- Paste in the "Manage Entity ID" you recorded earlier in the "Expose an API" section. Eg. api://string.
- If you plan to use SAML for authenticating users in Produce, you will need to complete ALL previous steps and take the same notes - use the API URL for the "Produce Entity ID" value.
- Paste in the "Metadata Url" you recorded earlier from the Endpoints section.
- Paste in the "Identity Provider Issuer" URL you recorded earlier from within the Federation Metadata XML document.
- Paste in the "Identity Provider Login URL" you recorded earlier from the Endpoints section.
- Change to "Upload certificate" and click Choose file. Locate the inifinit-ipc.cer file you created earlier and upload it.
- Set the "Infiniti Signing Algorithm" to RSA-SHA1.
- Tick "Log Mode"
- Click Save
Infiniti User Profile Mapping Configuration
Infiniti provides a screen for mapping user profile fields to SAML claims that are returned by Azure AD.
- In Intelledox Manage > Settings. Click User Profile Mapping.
- In a separate browser tab, open the Metadata Url and gather the appropriate Uri attributes to be mapped. Should be something like:
Uri="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"

Note that if you don’t wish to load Azure AD groups, remove the ‘Groups’ claim from the mappings and it will no longer require permission to access the Microsoft Graph API.
Once both Infiniti and Azure AD are configured you should be able to authenticate. If you wish to add any user groups, simply add them to the users in Azure AD, and also add the same names as groups in Infiniti and mark them as ‘External’ groups. Any groups assigned to a user in Azure AD that matches external groups configured in Infiniti will be assigned. All users are automatically assigned the ‘Infiniti User’ built-in group.
Find AttributesCTRL+F for
Extension Installation
- Request the Azure SAML files from Intelledox Support.
- Once received, on the web server hosting Infiniti, copy the following DLL files to the \Manage\bin (and \Produce\bin and if using SAML for Produce authentication too) folder/s. If your Infiniti instance is an Azure PaaS deployment, you will need to place these files in the relevant deployment folders and redeploy.
- AzureADSamlExtension.dll
- Microsoft.IdentityModel.Clients.ActiveDirectory.dll
- Microsoft.IdentityModel.Clients.ActiveDirectory.Platform.dll
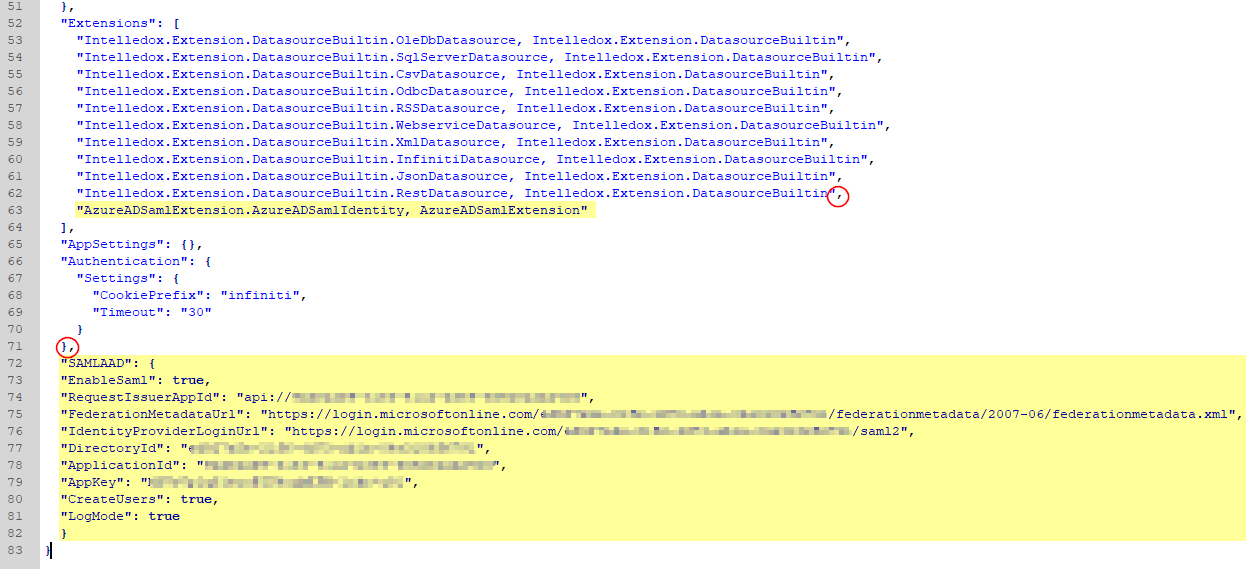
- Open the Manage appsettings.json located in the root of the Manage folder file add the following extension line to the end of the list of extensions, making sure there is a comma at the end of the extension above:
"AzureADSamlExtension.AzureADSamlIdentity, AzureADSamlExtension"- Add the following json block before the final closing curly brace “}” (again, ensuring there is a comma after the previous closing curly brace eg. "},". Refer to your recorded notes for all values.
"SAMLAAD": {
"EnableSaml": true,
"RequestIssuerAppId": "eg. api://string",
"FederationMetadataUrl": "eg. https://login.microsoftonline.com/string/federationmetadata/2007-06/federationmetadata.xml",
"IdentityProviderLoginUrl": "eg. https://login.microsoftonline.com/string/saml2",
"DirectoryId": "eg. string",
"ApplicationId": "eg. string",
"AppKey": "eg. client secret string",
"CreateUsers": true,
"LogMode": true
}
Note: that you will need to update the example values in above with details from your Azure AD configuration notes. See table below for more information about each option in the SAML AD section:
Option | Required | Description |
|---|---|---|
EnableSaml | N | Set to ‘true’ to enable SAML authentication, otherwise the system will default to another authentication method. |
Issuer | N | Optionally override the default Azure AD issuer URI, by default this is ‘https://sts.windows.net/{directoryid}/’ |
RequestIssuerAppId | Y | This is the Azure AD App ID URI value for the registered app. This can be found in the Azure portal by navigating to the registered app > Settings > Properties. |
FederationMetadataUrl | Y | Azure AD federation metadata URL can be found in the Azure portal by navigating to App Registrations > Endpoints and copying the Federation Metadata Document URL. (Refer below image - FederationMetadataUrl) |
IdentityProviderLoginUrl | Y | Login URL for SAML can be found in the Azure portal by navigating to App Registrations > Endpoints and copying the SAML-P Sign-On Endpoint. (Refer below image - IdentityProviderLoginUrl) |
DirectoryId | Y | Unique ID for the instance of Azure AD, can be found in the Azure portal by navigating to Properties from the main Azure AD screen. |
ApplicationId | Y | Unique ID for the registered app (Manage or Produce) in Azure Ad, can be found in the Azure portal by navigating to Azure Active Directory > App Registrations. (Refer below image -ApplicationId) |
AppKey | Y | Create a new password by navigating to App Registrations > (Your app) > Settings > Keys and creating a new password. Once created it will temporarily show you the password to copy. |
CreateUsers | N | Set to true to create permanent Infiniti user profiles. Default is true. |
LogMode | N | Set to true to log all SAML activity in the EventLog table in the Infiniti database. This logging is quite verbose so it is recommended that you keep this false unless troubleshooting. Default is false. |
Note: that any items marked not required can be left out of the config file if you wish to use their default values, except for ‘EnableSaml’ which is needed to turn on this feature.
Restart the Server or Server Instance (if Paas deployment)
Once both Infiniti and Azure AD are configured and the server has been restarted you should be able to authenticate.
- If you wish to automatically add users to AD's user groups, simply add the users to the groups in Azure AD, and also create groups in Infinit with exactly the same names as the Azure AD groups. Mark these new groups as ‘External’ groups.
- Any groups assigned to a user in Azure AD that matches external groups configured in Infiniti will be assigned.
- All users are automatically assigned the ‘Infiniti User’ built-in group.
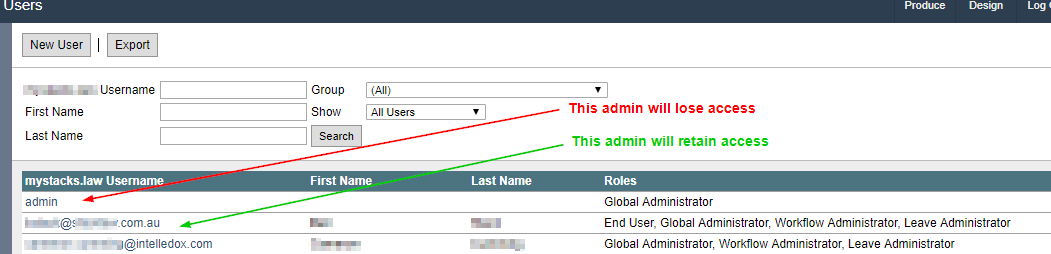
*Note that any if existing Infiniti users with Internal Authentication have a unique username (ie. not the same as their Azure AD email address), these users will no longer be able to login. Therefore it is advisable to have AT LEAST ONE internal user setup with the same username convention (email address) of an Azure AD user, and this user MUST HAVE GLOBAL ADMIN roles and permission or group membership to ensure continued access to the Manage side of Infiniti.*
Updated 8 months ago
