LDAP
Configuring LDAP Authentication
The LDAP Membership extension provides connectivity/subscription to an existing LDAP implementation for authentication, user profiles and group memberships. To authenticate and authorize a user Infiniti LDAP will request the following of the LDAP server:
- Authentication - Confirmation that a username and password credentials are correct. Depending on the LDAP implementation the username may require a domain.
- User Profile Query - User profile attributes such as names, emails etc.
- User Group Memberships Query - A list of groups that the user is a member of.
- Parent Group Memberships Query (recursive) - list of groups that a particular group is a member of (recursive).
As LDAP implementations are not standard the query filters can be configured to suit the environment.
How to Install LDAP
By default Infiniti Installations use Forms Authentication as the licensing and an administrator group must be set before LDAP can be configured.
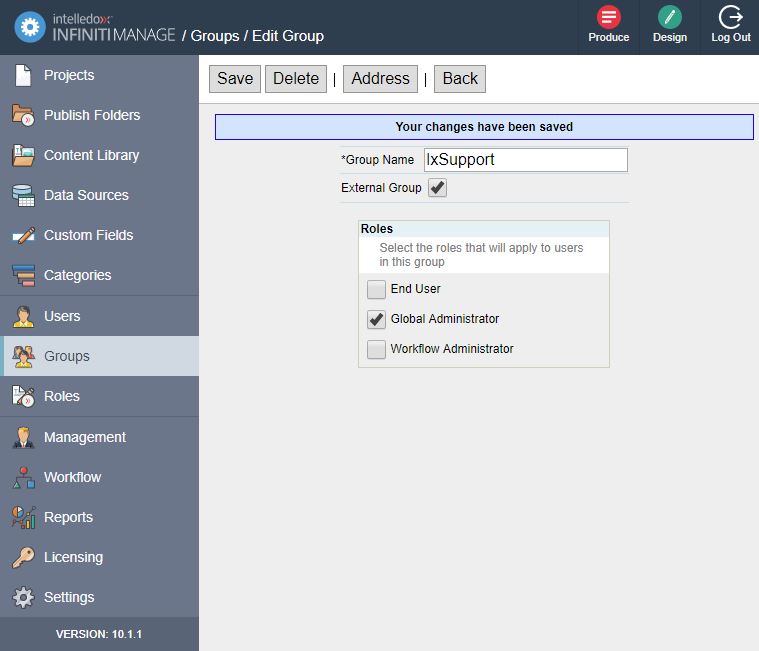
Step 1 - Identify and configure and LDAP Infiniti administrator group.
When the first user (usually a server administrator) is authenticated, Infiniti needs to assign them permissions so they can access appropriate functionality. If this step is not completed users will not be able to actually do anything post authentication. Use the article below to configure an external group.
Step 2 Modify the Produce and Manage Appsettings.Json files
From the Infiniti Web server open the Produce appsetings.json. file (usually similar to c:\inetpub\wwwroot\Infiniti\Produce\appsetings.json)
Firstly, Locate the Extensions Array, and add the following, line,
("Intelledox.Extension.IdentityBuiltin.LDAPIdentity, Intelledox.Extension.IdentityBuiltin")
Now Locate or create an Authentication/LDAP object, this is where the environment specific properties will be set. At a minimum add an "LdapPath" property, additonal properties are describe in the tables below.
Your AppSettings file should look similar to the below.
{
"ConnectionStrings": {
"DefaultConnection": "Password=infiniti;Persist Security Info=True;User ID=infiniti;Initial Catalog=Infiniti;Data Source=server1234"
},
"Extensions": [
"Intelledox.Extension.DatasourceBuiltin.OleDbDatasource, Intelledox.Extension.DatasourceBuiltin",
...
...
"Intelledox.Extension.IdentityBuiltin.LDAPIdentity, Intelledox.Extension.IdentityBuiltin"
],
"Authentication": {
"LDAP": {
"LdapPath": "LDAP://ldapServer",
"Username": "myServiceAccount",
"Password": "qwerty78"
}
}
}General Properties
Provide at least an LdapPath for the connection to LDAP.
Title | Example | Notes |
|---|---|---|
LdapPath | LDAP://ldapServer | Mandatory |
logging | true/false | See the logging section below for more information |
User Authentication Properties
The Authentication properties allow the specification of the auth type and also the format of the username.
Title | Example | Notes |
|---|---|---|
authenticationtype | Secure,none | Default = secure |
userauthusername | uid={{username}},dc={{domain}},dc=acme,dc=com | Syntax for how the username should be passed to the LDAP server for authentication. For example a user might enter their username as domain\username however it might be passed to the server as uid=username,dc=domain,dc=acme,dc=com |
LDAP Query Properties
Settings for validating the user’s supplied credentials.
Title | Example | Notes |
|---|---|---|
queryauthenticationtype | Secure,None,Anon | An authentication type to use when making LDAP queries to retureve user information such as profile and group membeships. Default = secure |
username | admin | Credentials will be used to query the LDAP server for the user’s profile and group membership information. Not required if read only access is permitted by your LDAP sever. |
password | secret#1234 | Credentials will be used to query the LDAP server for the user’s profile and group membership information. Not required if read only access is permitted by your LDAP sever. |
User Profile Query
Query to retrieve user data such as name, email, address etc.
Title | Example | Notes |
|---|---|---|
userldappath | LDAP://Intelledox/OU=Users,OU=Org,DC={{domain}},DC=local | A specific path to provide when making the user profile query, limiting the query’s scope to save time. |
userfilter | (& (ObjectClass=person)(sAMAccountName={{username}})) | The LDAP filter passed used to find exactly one user |
Group Membership Attribute
Use when groups memberships are sourced from the above user profile. (DEFAULT)
Title | Example | Notes |
|---|---|---|
usergroupmembershipattribute | MemberOf | An attribute name that represents a group membership sourced from the user’s profile. |
Group Membership Entities Query
Use when group memberships are sourced from a separated query
Title | Example | Notes |
|---|---|---|
usergroupldappath | LDAP://SERVER/dc={{domain}},dc=acme,dc=com | A specific path to provide when making the group membership entity query, limiting the query’s scope to save time. |
usergroupentitiesfilter | (& &(objectclass=groupOfNames)(member{{username}})) | A filter that must return one or more results. I.e. one or more groups that the user is a member of. |
the user is a member of. | Cn | When the groups are returned the usergroupnameattribute represents the attribute to source the name from. Default = cn |
Parent Groups
Recursive query to search for parent groups
Title | Example | Notes |
|---|---|---|
parentgroupldappath | LDAP://SERVER/dc={{domain}},dc=simo,dc=com | A specific path to provide when making the user profile query, limiting the query’s scope to save time. |
parentgroupentityfilter | (&(ObjectClass=group)(sAMAccountName={{groupname}})) | The LDAP filter passed used to find exactly one group |
parentGroupMembershipAttribute | MemberOf | Default =MemberOf |
LDAP SYNC
Title | Example | Notes |
|---|---|---|
syncldappath | LDAP://server | |
syncgroupfilter | (&(objectCategory=group)(cn={{groupname}})) | Default (&(objectCategory=group)(cn={{groupname}})) |
syncgroupdistinguishednameattribute | distinguishedName | Default |
syncparentgroupfilter | (&(ObjectCategory=group)(memberof={{groupdistinguishedname}})) | Default |
syncmemberfilter | (&(ObjectCategory=person)(memberof={{groupdistinguishedname}})) | Default |
syncmemberusernameattribute | samAccountName | Default |
syncmemberdistinguishednameattribute | distinguishedName | Required if domain required. |
Logging
Where logging is configured, results are stored in the Infiniti database. Can be retrieved using the following SQL statement.
SELECT TOP(10)*
FROM EventLog
ORDERBY [DateTime] DESCUpdated 9 months ago