OpenID Connect
Interface Feature AvailabilityAvailable in web interfaces Produce, Manage and Design only.
Overview
OpenID Connect (OIDC) is an identity layer that sits on top of OAuth 2.0. SmartIQ supports the use of OpenID Connect as a relying party (RP) using the following authentication flows:
- Authorization Code Flow (recommended)
- Implicit Flow
- Hybrid Flow
Setting the Response Type will determine which flow the software will take. The response types set in SmartIQ must also be supported by the identity provider. Check the identity provider documentation and associated metadata document to confirm.
Flow | Response Type value |
|---|---|
Authorization Code Flow | code |
Implicit Flow |
|
Hybrid Flow |
|
OpenId Connect Logout SupportOpenID only supports logout if the IDP metadata has an
end_session_endpointvalue. The login also needs to return anid_tokenvalue for the Log Out link to appear. This is required for the IDP to know what session is being logged out of.
Configuration
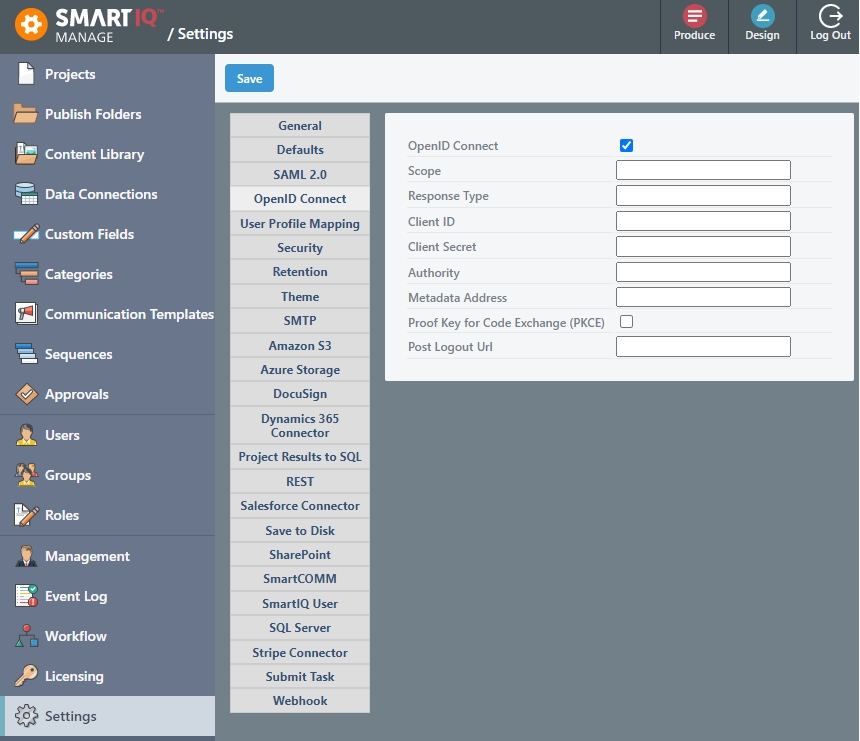
Multi-tenant cloud customers can configure OpenID Connect from Manage. They cannot be set if SAML 2.0 is already enabled. Check the OpenID Connect checkbox to enable these settings for Produce and Manage.
NoteThe Proof Key for Code Exchange (PKCE) option will only be available for multi-tenant sites. Enabling this option passes the
code_challengeandcode_challenge_methodparameters to the login for additional security.
For on-premise and hosted instances, OpenID Connect configuration options are set in the appsettings.json file for Produce and Manage.
"Authentication": {
"OpenIDConnect": {
"ClientId": "...",
"ClientSecret": "...",
"Authority": "...",
"MetadataAddress": "...",
"Scope": "...",
"ResponseType": "...",
"PKCE": "...",
"PostLogoutUrl": "..."
}
}Attributes
Attributes required will vary based on the flow type but are common across deployment types.
Attribute | Description |
|---|---|
ClientId (Required) | Unique id that represents this application. |
ClientSecret | Shared secret to prove the request comes from right app. |
Authority (Required) | URL to redirect to the identity provider. For example, Google https://accounts.google.com/, Azure https://login.microsoftonline.com/{tenant} Also known as the issuer depending on the identity provider. |
MetadataAddress | URL to the configuration documentation. This configures the authentication. The web server must be able to request this URL. If empty, will follow the OpenId Connect standard of appending ".well-known/opened-configuration" to the "Authority" value. |
Scope | The types of claims to request from the IDP. By default only "openid" is requested. If this configuration has a value, then the first value must be "openid". Other values are space delimited. For example, "openid profile email" |
ResponseType (Required) | Set to the appropriate values to perform the flow required. |
PostLogoutUrl | Redirect the browser to this URL when the user logs out of Produce. This can be a company website or some other portal. If no value is entered, Produce will redirect to |
Creation and Deletion of Users
If a user doesn't already exist in SmartIQand they attempt to login, a SmartIQ user account will be automatically created for that user on successful authentication.
Deletion of users should be done via the API.
Identity Provider Configuration
When configuring applications for SmartIQ within your chosen identity provider, you will need the Redirect Uri for Manage and Produce. The format is, your SmartIQ domain appended with the following:
- Manage
/manage/signin-oidc/manage/signout-callback-oidc
- Produce
/produce/signin-oidc/produce/signout-callback-oidc
For example, <https://sample-tenant.ab12.smartcommunications.cloud/produce/signin-oidc> and <https://sample-tenant.ab12.smartcommunications.cloud/produce/signout-callback-oidc> .
Also consider the following:
- The most common error message from the identity provider will be a redirect_uri mismatch. This means the uri registered against the application in the identity provider doesn't match your domain or the format above.
- OpenID Connect requires HTTPS to be enabled on the identity provider and SmartIQ when not using localhost.
- The default claims that are supported are sub, name, email, given_name, family_name, phone_number. Others can be mapped in Manage > Settings > User Profile Mapping.
The claims must be returned within the id_token to be extracted and used for mapping.
Updated 10 months ago
