Windows Authentication
Deployment Feature AvailabilityAvailable in on-premise deployments only.
Interface Feature AvailabilityAvailable in web interfaces Produce, Manage and Design. Also available in Infiniti GO iOS and Windows only.
Windows Authentication uses Windows Active Directory to authenticate and authorize users into the {user.productname} platform. User credentials are automatically retrieved based on who the user has logged onto the machine as they are not prompted for a username or password.
Windows authentication automatically retrieves profile information such as their name and email address as well as subscribes (and unsubscribes) to groups automatically authorizing access to particular forms and administrative features.
End users must belong to the same domain as the {user.productname} web server, or to a trusted domain.
Appropriate AD groups need to be added to{user.productname}before users open the site so that users can be authorized as needed by the business. For example:
- Give the 'Domain_Admins' group Global Administrator privileges
- Give the 'Internal_HR' group access to the onboarding and exit forms
If no appropriate external group exists in{user.productname}to match the AD groups, the AD login will not work for affected users.
How to Enable Windows Authentication
By default, {user.productname} installations use Forms Authentication and an administrator group must be added before Windows Authentication can be configured.
Step 1: Identify and Configure an Active Directory SmartIQ Administrator Group
When the first user (usually a server administrator) attempts access, {user.productname} needs to assign necessary permissions so they can access appropriate functions. To ensure that users can make changes post authentication, use the following article to configure External Authentication User Groups.
If this step is not completed users will not be able to actually do anything post authentication.
Tip: Start with ProduceIsolate Windows authentication to the Produce application only, initially, to test configuration settings. This is so that if any configuration settings need to be changed in Manage, it is possible to make changes under forms authentication.
Step 2: Add WindowsIdentity to Manage and Produce
- Open the
appsettings.jsonfile in the Manage folder. - Find the
Extensionssection of the file and addWindowsIdentityto the end of that section:
,
"Intelledox.Extension.IdentityBuiltin.WindowsIdentity, Intelledox.Extension.IdentityBuiltin"- Open the
appsettings.jsonfile in the Produce folder. - Find the
Extensionssection of the file and addWindowsIdentityto the end of that section.
Step 3: Configure IIS
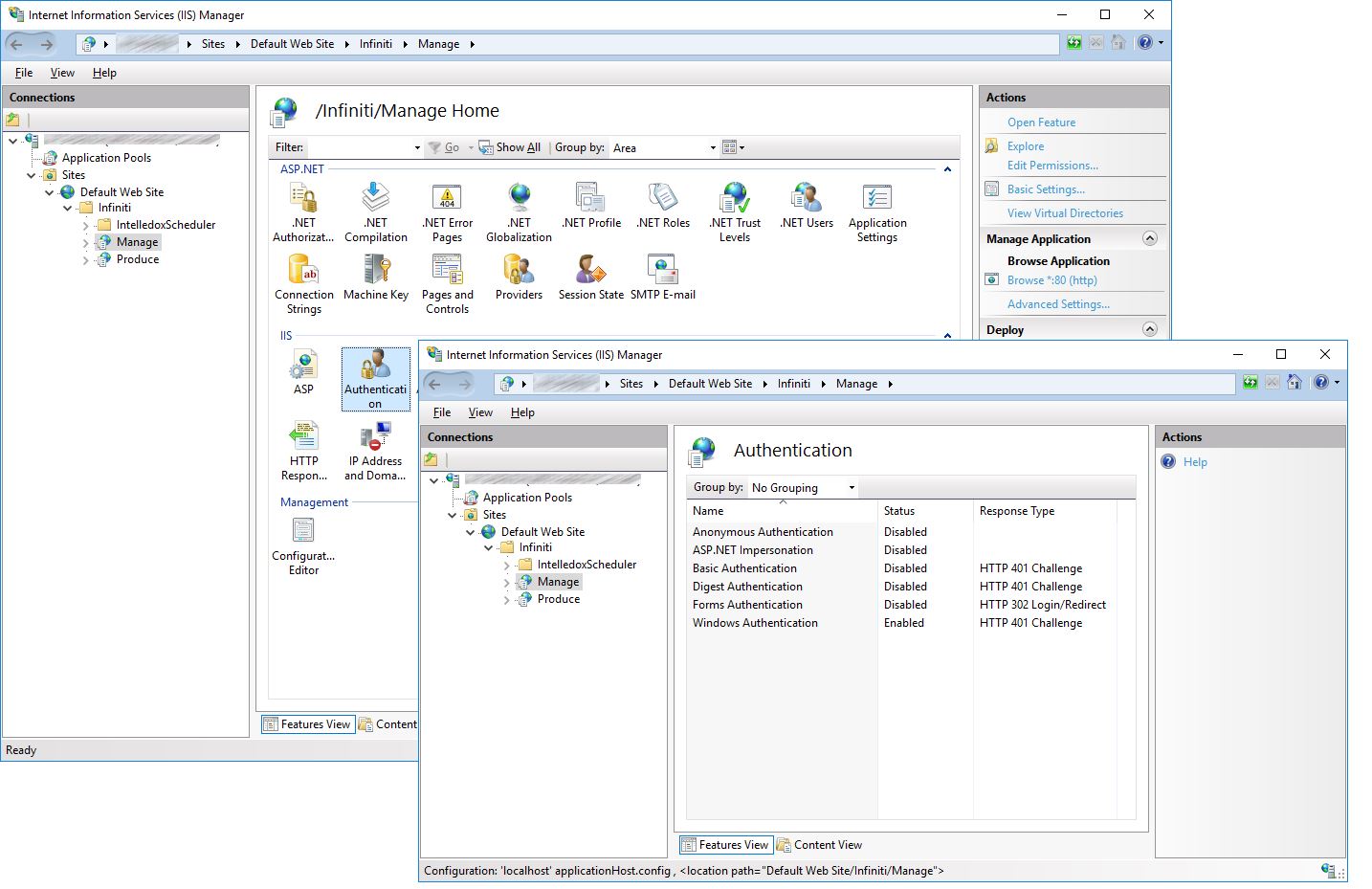
- From the web server IIS, expand the connections tree until the Manage and Produce Application appears.
- Double-click the Authentication Icon.
- Ensure Windows Authentication is the only item enabled.
Step 4: (Optional) Appsettings.json Setting Configurations
The following settings can be configured to suit the environment where necessary.
- From the
{user.productname}Web server, open the Manageappsettings.jsonfile (usually similar to*c:\inetpub\wwwroot\<<productname>>\Manage\appSettings.json*) - Add and configure and Authentication object as per the table and example below:
Setting | Description | Example Setting |
|---|---|---|
NestedGroups | Gives the option to check the group memberships the user is a member of. When this option is off, only the groups the user is directly a member of will be checked against The default is 'true'. | True/False |
ADPath | This setting overrides the default directory search path of "LDAP://mydomainname". The domain name used comes from the user's Windows credentials (Eg: mydomainname\user123). This might not be the correct or quickest place to perform AD queries, so use this setting to specify an alternate path. | LDAP://server.local |
KeepDomain | When set to True, accounts will be created in the format "domain\username." This attribute enables Multi-Domain support when usernames are not unique between domains. Default is false. | True/False |
Logging | A logging mode where verbose logging information is written to the | True/False |
UpdateExternalGroupMembership | Adds users to their respective external groups in Additionally, if their membership in the AD changes, this will update their membership in Running this Sync with this option enabled can take several minutes to finish, and is highly dependent on the number of users in the AD. | True/False |
ReplaceIdentity | To enable Anonymous Authentication along with Windows Authentication this setting must be True. The default value is False. If ReplaceIdentity is True, you also need to ensure that | True/False |
AutoCreateUser | Allows the automatic creation of a user if a valid Active Directory user accesses the system. The default value is False. | True/False |
{
"AppSettings": {
"PortalURL": "",
"ProduceURL": "http://server/Produce/"
},
"ConnectionStrings": {
"DefaultConnection": "Password=XXXXXXXX;Persist Security Info=True;User ID=XXXXXXXX;Initial Catalog=Dev;Data Source=server123",
"DboConnection": "Password=XXXXXXXX;Persist Security Info=True;User ID=XXXXXXXX;Initial Catalog=Dev;Data Source=server123"
},
"Extensions": [
"Intelledox.Extension.DatasourceBuiltin.OleDbDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.SqlServerDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.CsvDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.OdbcDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.RSSDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.WebserviceDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.XmlDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.InfinitiDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.JsonDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.DatasourceBuiltin.RestDatasource, Intelledox.Extension.DatasourceBuiltin",
"Intelledox.Extension.IdentityBuiltin.WindowsIdentity, Intelledox.Extension.IdentityBuiltin"
],
"Authentication": {
"Settings": {
"CookiePrefix": "",
"Timeout": "30"
},
"Windows": {
"KeepDomain": "False",
"Logging": "False",
"NestedGroups": "True",
"ADPath": "LDAP://Server.local",
"UpdateExternalGroupMembership": "True",
"ReplaceIdentity": "False"
}
}
}Step 5: Test
User GroupsA user's group memberships can be retrieved via a net user command.
net user yourUser /domain
net user johnd /domain
- Ensure you are logged in as a user that is a member of the AD group created in Step 1.
- Close all browsers to ensure any existing
{user.productname}sessions are removed. - Open a new browser and navigate to
{user.productname}Manage or Produce. - You should be logged in to Manage or Produce Home respectively.
User Profile Mapping
Users can set up user profile mapping in Manage > Settings > User Profile Mapping for Windows authenticated environments.
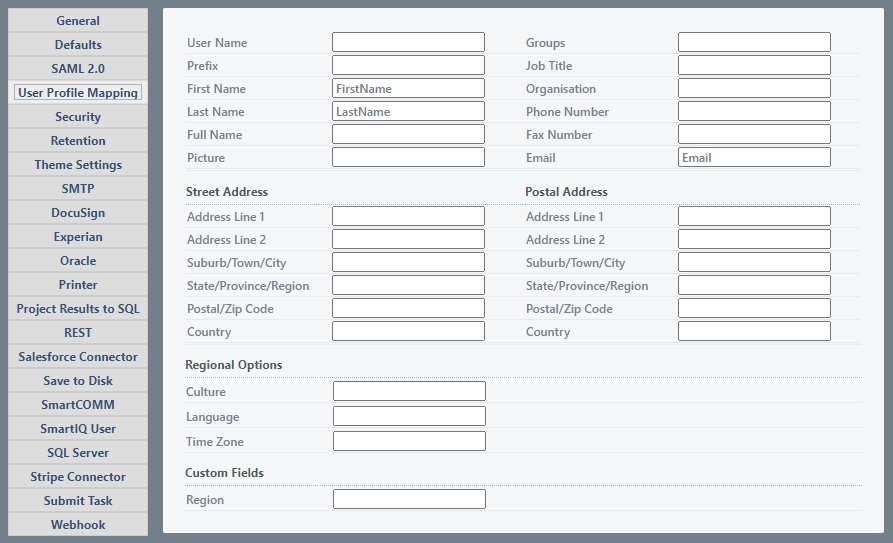
{user.productname}s windows identity provider will respond to the defined user profile mapping. The identity provider will try and match the field name in {user.productname} to the corresponding field in the Active Directory. If the field does not exist in the AD, the user property will remain empty and logging will indicate this failure when turned on.
Defined standard fields Username, First Name, Last Name and Email address are populated by default with the corresponding AD fields. These standard fields will be overwritten if a mapping field is defined.
Following is the example of error log displayed in {user.productname} if the defined user mapping field is not present in the Active directory:
WINDOWS AUTHENTICATION VALIDATE START
Domain: 'Domain'
Username: 'UserA'
DomainUser: 'UserA'
directoryPath: 'LDAP://Server.local'
GROUP QUERY (GroupA)
Filter: (&(ObjectClass=group)(sAMAccountName=GroupA))
Query: 14.96ms
PRIMARY GROUP SEARCH
filter '(objectSID=\01\05\00\00\00\00\00\05\15\00\00\00\46\f0\c8\3e\8e\0e\83\f8\4b\ea\4c\77\01\02\00\00)'
Query: 13.9624ms
AD user and matching SmartIQ groups found
User mapping field: Phone not found. Please ensure that the User mapping corresponds to an Active Directory existing field.
User mapping field: Fax not found. Please ensure that the User mapping corresponds to an Active Directory existing field.
User mapping field: displayname found.Synchronising Users
Manual Sync
To manually synchronise all users in the AD groups you have created, use the Manage > Users > Sync button. This button will only appear if Windows Authentication is enabled.
Manual sync uses the Windows account of the user logged into Manage. This user must have permissions to read all the relevant AD groups to correctly sync all users.
Automating Sync
The sync process can be automated to run once daily using the Scheduler. To configure this:
-
Open the
appsettings.jsonfile in the Scheduler folder. -
Find the
Extensionssection of the file and add the following to the end of that section:
,
"Intelledox.Extension.IdentityBuiltin.WindowsIdentity, Intelledox.Extension.IdentityBuiltin"- Copy the Windows settings you created in Step 4 above into the Authentication section of the Scheduler
appsettings.jsonas well. You may need to create the Authentication section. It will look something like this:
,
"Intelledox.Extension.IdentityBuiltin.WindowsIdentity, Intelledox.Extension.IdentityBuiltin"
],
"Authentication": {
"Settings": {
"CookiePrefix": "",
"Timeout": "30"
},
"Windows": {
"KeepDomain": "False",
"Logging": "False",
"NestedGroups": "True",
"ADPath": "LDAP://server.local".
"ADName": "myservershortname"
}
}Note that an additional attribute "ADName" has been added to the Windows section. You need to set this to the server short internal domain name. This is the left (domain) part of the domain\myusername that users login to your Windows AD with.
Once configured, the sync will run once daily at the first run of the Scheduler after midnight each day. You can also run this manually from the Scheduler by executing the scheduler from the console (if the process has not already run that day).
See Using Scheduler for more information about configuring and running the Scheduler.
Manual sync uses the Windows account that the Scheduler process if running under. This user must have permissions to read all the relevant AD groups to correctly sync all users.
WarningThe synchronisation process will only work for the main AD domain and not for trusted domains.
Logging and Troubleshooting
With the logging setting in Step 4 above enabled, logs can be retrieved from the {user.productname} database using the following SQL query.
SELECT *
FROM EventLog
ORDER BY DateTime DESCAn example working log is provided below.
WINDOWS AUTHENTICATION VALIDATE START
Domain: 'Domain'
Username: 'user123'
DomainUser: 'user123'
directoryPath: 'LDAP://Server.local'
USER PROFILE QUERY
Filter: (&(ObjectClass=person)(sAMAccountName=user123))
Query: 453.4937ms
GROUP QUERY (GroupX)
Filter: (&(ObjectClass=group)(sAMAccountName=Ix_GroupX))
Query: 31.2193ms
GROUP QUERY (GroupY)
Filter: (&(ObjectClass=group)(sAMAccountName=Email-GroupY))
Query: 0ms
GROUP QUERY (IxSupport)
Filter: (&(ObjectClass=group)(sAMAccountName=IxSupport))
Query: 15.6266ms
PRIMARY GROUP SEARCH
filter '(objectSID=\01\05\00\00\00\00\00\05\15\00\00\00\46\f0\c8\3e\8e\0e\83\f8\4b\ea\4c\77\01\02\00\00)'
Query: 22.1467ms
AD user and matching SmartIQ groups foundWINDOWS AUTHENTICATION VALIDATE START
Domain: 'Domain'
Username: 'user123'
DomainUser: 'user123'
directoryPath: 'LDAP://Server.local'
USER PROFILE QUERY
Filter: (&(ObjectClass=person)(sAMAccountName=user123))
Query: 453.4937ms
GROUP QUERY (GroupX)
Filter: (&(ObjectClass=group)(sAMAccountName=GroupX))
Query: 31.2193ms
GROUP QUERY (GroupY)
Filter: (&(ObjectClass=group)(sAMAccountName=GroupY))
Query: 0ms
GROUP QUERY (ChangedName)
Filter: (&(ObjectClass=group)(sAMAccountName=ChangedName))
Query: 15.6266ms
PRIMARY GROUP SEARCH
filter '(objectSID=\01\05\00\00\00\00\00\05\15\00\00\00\46\f0\c8\3e\8e\0e\83\f8\4b\ea\4c\77\01\02\00\00)'
Query: 12.0327ms
No matching SmartIQ groups foundUpdated 10 months ago
