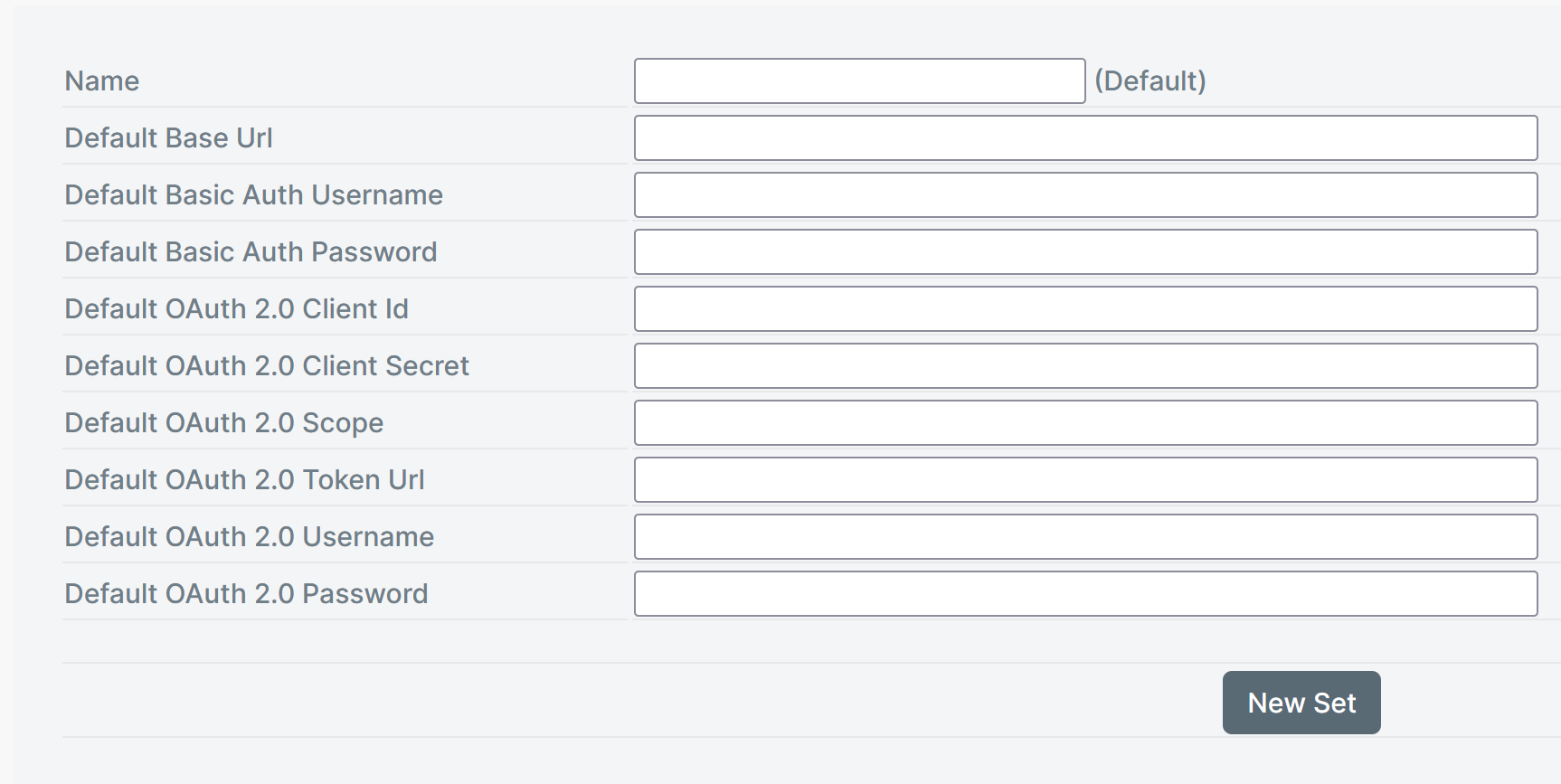
REST Configuration Settings
Note
If the OAuth Client Id has a value, then all REST extensions for that named set will use OAuth.
Multiple Accounts
Click the New Set button to create additional accounts. For example, Sandbox and Production. Additionally, click the Set as Default button to change the default connector set. If the previous Default was set in Design, SmartIQ will now use the new Default connector values.
Authentication Options
Authentication tokens are cached for up to one day or until the token has expired, whichever comes first.
Basic
For basic authentication just provide a username and password, this is a HTTP header with the user and pass encoded in base64.
Windows
Windows Authentication (Active Directory) has to be enabled in SmartIQ instance.
Access Token
Access Token (OpenID Connect & SAML) authentication's ResponseType can be configured to retrieve an access_token returned from the IDP. This access_token can be passed to external APIs as authentication as the current user.
OAuth 2.0 Client
OAuth 2.0 Client Credentials grant type allows the entry of the Client Id, Client Secret and Scope. The Client Credentials grant is used when applications request an access token to access their own resources, not on behalf of a user.
SmartIQ will automatically retrieve the access token from the token endpoint and cache it until expiry. Each request to the target REST endpoint will include the access token from the cache (or retrieve a new one) in requests as a bearer token header.
The global Token Url can be overridden per datasource in the Connection Attributes or within the security Definitions section of the swagger or the openapi spec.
- In the Connection Attributes the Token Url is specified with the parameter oauthTokenUrl eg:
oauthTokenUrl=<https://mytokenurl> - In the Definitions section of the swagger or openapi spec the parameter clientCredentials should be set to the token url.
OAuth 2.0 Resource Owner Password Credentials
The REST Action, REST Escalation and REST Data Connection support OAuth 2.0 Resource Owner Password Credentials Grant type.
Use this function only as a last resort and only if more secure flows are not possible
This flow requires a very high degree of trust in the application, and carries risks which are not present in other flows as the resource owner’s password is exposed to the application.
The Resource Owner Password grant is used when trusted applications requests an access token to access their own resources, not on behalf of a user. SmartIQ will automatically retrieve the access token from the token endpoint and cache it until expiry.
Each request to the target REST endpoint will include the access token from the cache (or retrieve a new one) in requests as a bearer token.
If a username input on an Action of Escalation has a value then resource owner flow will be used.
The global Token Url can be overridden per datasource in the Connection Attributes or within the security Definitions section of the swagger or the openapi spec.
- In the Connection Attributes the Token Url is specified with the parameter oauthTokenUrl eg:
oauthTokenUrl=<https://mytokenurl> - In the Definitions section of the swagger or openapi spec the parameter password should be set to the token url.
No Credentials Required
Custom Headers can be used to specify Authorization Header values. See REST connector on using Custom Headers.
Updated about 1 month ago
